Nachfolgend werden Ihnen die wichtigsten Vorschläge zur besseren Absicherung ihrer Computer vorgestellt. Werden diese umgesetzt, haben es Cyber-Angreifer_innen erheblich schwerer, Sie und Ihre Daten in Gefahr zu bringen.
Nachstehend sind die wichtigsten Punkte zusammengefasst:
- Backup: Erstellen Sie regelmäßig ein Backup welches Sie an einem sicheren Ort verwahren. Alle aktuellen Betriebssysteme haben bereits entsprechende Sicherungstools kostenlos integriert.
- Sichere Passwörter: Diese sind der Schlüssel zu unserer digitalen Identität. Um gegen moderne Angriffe bestmöglich geschützt zu sein, sollten sie zumindest 12 Zeichen lang und vor allem nur einzigartig (für jeden Dienst ein eigenes Passwort) sein. Mithilfe von Passätzen, ist dies leicht für jeden umzusetzen.
- Virenschutz: Jeder Rechner muss durch einen aktuellen Virenscanner vor bekannten Bedrohungen geschützt werden.
- Systemupdates: Hersteller beheben regelmäßig kritische Schwachstellen in ihren Softwareprodukten. Damit ein Rechner geschützt ist, müssen Updates sobald wie möglich installiert werden.
- Festplattenverschlüsselung: Um unautorisierte Datenzugriffe zu verhindern, wird empfohlen, die Festplatten aller Endgeräte zu verschlüsseln.
- Bildschirmsperre: Damit ein Rechner bei Abwesenheit entsprechend geschützt ist, sollte eine automatische Bildschirmsperre eingerichtet sein.
- Office Makros: Diese Automatisierungsfunktion wird sehr häufig für die initiale Malwareinfektion missbraucht. Darum wird empfohlen, Sie von vornherein zu deaktivieren.
- Bewusste Wahl eines Standardbrowsers: Der Browser ist unser Tor in die unendlichen Weiten des Internets. Umso wichtiger ist es, dass wir uns explizit für eine sichere und vom jeweiligen Hersteller gewartete Software entscheiden. Empfohlen werden Firefox, Google Chrome und Microsoft Edge.
- Dateierweiterungen anzeigen & erkennen: Windows „erkennt“ die unterschiedlichen Dateien anhand ihrer Dateierweiterung. Diese soll im Windows Explorer angezeigt und richtig gedeutet werden.
- Separate_r Admin-Benutzer_in: Das eigene Benutzer_innenkonnto sollte nicht mit administrativen Berechtigungen ausgestattet sein. Stattdessen wird die Einrichtung eines separaten Admin-Kontos empfohlen.
- Pro-Tipp: PowerShell absichern: Windows integriert diese sehr mächtige Skriptsprache, die bei vielen Angriffen zur Anwendung kommt. Mit dem Constrained Language Mode ist eine Absicherung möglich.
Allgemeines
Egal ob Online Banking, Facebook, Instagram oder E-Mail: die Digitalisierung ist nicht nur im beruflichen Leben, sondern auch im Privatbereich sehr präsent. Dies bringt, neben vielen Möglichkeiten die uns den Alltag erleichtern, auch Risiken mit sich. So hören wir laufend von Cyber-Angriffen denen Unternehmen, staatliche Einrichtungen und Privatpersonen zum Opfer fallen. Die Erfahrung zeigt, dass jede_r zum Ziel einer Attacke durch Hacker_innen werden kann. Niemand ist „zu unwichtig“!
Neben klassischen Social Engineering Techniken, bei denen Benutzer_innen beispielsweise zur Preisgabe sensibler Informationen verleitet werden sollen, nutzen Angreifer_innen auch technische Tricks, um Schadsoftware auf den Rechnern Ihrer „Kunden“ zu platzieren. Über diese Schadsoftware ist es anschließend möglich, alle gespeicherten Dateien (z.B. die neusten Auswertungen zu einem Forschungsprojekt oder Fotos des letzten Urlaubs) als digitale Geisel zu nehmen und für deren Freigabe ein Lösegeld zu fordern. Alternativ dazu kann aber auch der „eroberte“ Rechner verwendet werden, um illegale Inhalte zu verteilen oder die Schadsoftware manipuliert die nächste Onlinebestellung und kann so sensible Konto- bzw. Kreditkartendaten stehlen.
Um solche Szenarien zu verhindern, geben wir Ihnen Absicherungsempfehlungen, die helfen, einen Rechner vor Schadsoftware und technischen Attacken besser zu schützen. Nehmen Sie sich die Zeit und sichern sie Ihren Rechner im Büro, aber auch Ihren privaten Rechner ab, um zu vermeiden, dass Sie selbst zum Opfer werden.
1. Die Absicherung: Backup
Die Vorbereitung und Vorbeugung von Notfällen ist in vielen Bereichen bereits Normalität. So gehören beispielsweise gut platzierte und regelmäßig gewartete Feuerlöscher zur Grundausstattung jedes öffentlichen Gebäudes. Es gibt regelmäßige Evakuierungsübungen, Brandmelder werden auf ihre Funktionalität hin geprüft und jede Abteilung muss eine_n Brandschutzwart nominieren, der_die über eine entsprechende Ausbildung verfügt. Und natürlich gibt es die Feuerwehr als „Backup“, die alles daransetzt, das Schlimmste zu verhindern. Ein Zustand der 100%igen Sicherheit ist zwar nicht möglich, es ist aber möglich, sich auf den schlimmsten Fall vorzubereiten, um im Falle des Falles kühlen Kopf bewahren und die wichtigsten Dinge retten zu können. Dieses Bewusstsein über mögliche Risiken und Gefahren und deren Vorbeugung muss auch in den digitalen Alltag Einzug finden.
Der Erste und wichtigste Schritt dazu, ist das regelmäßige Erstellen von Backups (= Sicherungskopien).
Dabei müssen die wichtigsten Daten auf ein externes Speichermedium, wie beispielsweise einen USB-Stick, kopiert werden. Der USB-Stick muss dann an einem sicheren Platz aufbewahrt werden. Wichtig ist, dass das jeweilige Backup nicht am Rechner angesteckt bleibt, denn wenn es zu einem Cyber-Angriff kommt, ist auch die Sicherungskopie davon betroffen. Auch mechanische Schäden am exteren Speichermedium können durch eine räumliche Trennung verhindert werden.
Für die automatische Erstellung eines Backups ist heute auch keine teure Software mehr notwendig – ein USB Stick oder eine externe Festplatte mit genügend freiem Speicher sind ausreichend. Unter Apple Geräten kann für die eigentliche Sicherung die bereits integrierte Lösung „Time Machine“ verwendet werden[1].
Für Windows Nutzer_innen gibt es ebenfalls eine integrierte Sicherungslösung, den sogenannten „Dateiversionsverlauf“ (ab Windows 10). Dieses Feature kann verwendet werden, um die eigenen Dateien auf einer externen Festplatte oder aber auch auf einem Netzlaufwerk (im Unternehmen) zu sichern.
Konfiguration der Windows-Sicherung :
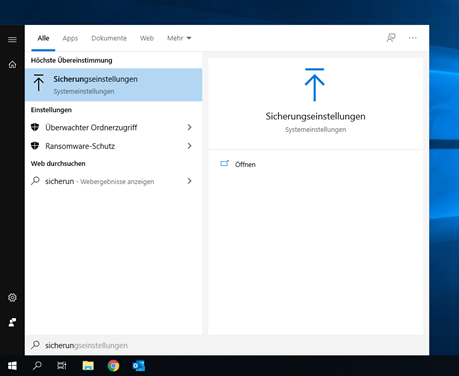
- Öffnen Sie das Windows Startmenü und suchen Sie über das Suchfenster nach dem Begriff „Sicherungseinstellungen“ (in Englisch: „File History“).
Abb. 1: Windows Sicherungseinstellungen
2. Stecken Sie Ihr externes Sicherungsmedium an oder verbinden Sie das Netzlaufwerk auf welchem das Backup erstellt werden soll.
3. Im nächsten Schritt wird das Sicherungsmedium als solches aktiviert. Dazu im Fenster „Sicherung“ das zuvor angesteckte Laufwerk auswählen. Ab diesem Zeitpunkt wird automatisch, sobald das Sicherungsmedium verfügbar (also angesteckt) ist, ein Backup erstellt. Da der erste Durchlauf längere Zeit in Anspruch nimmt, empfiehlt es sich, den Rechner beispielsweise über Nacht eingeschaltet zu lassen.
Abb. 2: Sicherung aktivieren
4. In der Standardkonfiguration werden alle Dateien aus dem eigenen Benutzerverzeichnis (z.B. dem Desktop oder den Dokumenten) gesichert. Haben Sie wichtige Inhalte auch in anderen Ordnern abgelegt, empfiehlt es sich, diese ebenfalls in die Sicherung miteinzubeziehen. Über die „Weiteren Optionen“ (siehe obigen Screenshot) können beliebige weitere Verzeichnisse in das Backup miteinbezogen werden.
Abb. 3: Sicherungsoptionen
Wichtig ist, dass Sie regelmäßig einen Sicherungsvorgang durchführen. Den aktuellen Status können Sie immer über die Anwendung „Dateiversionsverlauf“ selbst prüfen. Vergessen Sie nicht, das Sicherungsmedium nach erfolgreichem Abschluss des Vorgangs abzustecken und an einem sicheren Ort zu verwahren![2]
Windows erinnert Sie in regelmäßigen Abständen daran, eine Sicherung durchzuführen.
2. Sichere Passwörter
Beim Verlassen des eigenen Hauses oder der Wohnung, ist es selbstverständlich diese abzuschließen, sodass fremden Personen der Zugang erschwert wird. Online verwenden wird dazu statt eines Schlüssels Passwörter. Diese müssen (wie auch unser Schlüsselbund) vor missbräuchlicher Verwendung bewahrt werden.
Ein besonderes Risiko ist dabei der indirekte Passwort-Diebstahl. Wird etwa ein Onlineanbieter gehackt bei dem wir ein Benutzerkonto haben, kann das dazu führen, dass unser Passwort im Internet veröffentlicht wird. Nutzen wir dieses auch bei anderen Diensten, können Kriminelle nun auch darauf zugreifen. Daher müssen einerseits von Haus aus sichere Passwörter eingesetzt werden und andererseits muss für jeden Dienst ein eigenes verwendet werden. Aber: Wie soll man sich das alles merken?
Die Lösung dafür ist die Verwendung von sogenannten „Passsätzen“. Dabei werden leicht zu merkende Sätze verwendet, um ein komplexes und entsprechend langes (mind. 12 Zeichen langes) Passwort zu erzeugen, welches möglichst leicht zu merken ist. Hier ein Beispiel:
Der Satz soll einfach sein:
Damit nicht alle Dienste das gleiche Passwort erhalten, kann beispielsweise der Name des jeweiligen Anbieters in den Satz eingebaut werden: Ich kann mir Passwörter immer so schlecht merken, außer für Amazon!
Die Anfangsbuchstaben der einzelnen Wörter ergeben ein sicheres Passwort: |
Über die Webseite https://haveibeenpwned.com/ kann jeder selbst überprüfen, ob er oder sie bereits von einem indirekten Passwort-Diebstahl betroffen ist. Moderne Passwort-Manager, wie 1Password (https://1password.com/de/), verfügen über einen automatischen Passwort Qualitätscheck, sowie einen Abgleich mit öffentlich bekannten Datenleakst. Also ein guter Grund, einen Passwort-Manager einzusetzen.
| Bezeichnung | 1password |
|---|---|
| Internet-Adresse | https://1password.com/de/tour/ |
| Direkt-Einstieg | https://teamtuwien.1password.eu/signin |
| Art des Tools | Passwort Manager |
| Beantragung / Bestellung | |
| Kosten | € 5 Miete/Quartal - Bezug über CSW der TU.it |
| How-To | Beschreibungen |
Passwortmanager
Kurzbeschreibung
1password ist ein Passwort-Manager, der über die TU.it bezogen werden kann. Bei der Implementierung wurde darauf geachtet, eine gemeinschaftliche Nutzung innerhalb der TU Wien zu ermöglichen. In TISS angelegte und mit 1password synchronisierte upTUdate-Gruppen könnten zur Rechteverwaltung der einem Strukturelement zugeordneten, geteilten Tresor verwendet werden. Diese geteilten Tresore können von IT-Administrator_innen mit Rechten belegt werden.
Es werden zwei Campussoftware-Produkte angeboten:
- 1password-Teammitglied
- 1password-Gruppenadiministrator_in
Nur ein_e Gruppenadministrator_in kann geteilte Tresore (→ gemeinsame Nutzung durch mehrere Personen) erzeugen. Der_die Gruppenadministrator_in hat initial die Besitzrechte über einen geteilten Tresor. Änderungen im geteilten Tresor werden in der 1password-Webkonsole im Aktivitätenprotokoll angezeigt und sind somit jederzeit nachvollziehbar.
Mitarbeiter_innen der TU Wien können 1password auch privat nutzen und so ihre eigenen Passwörter sicherer gestalten. Jede Lizenz der TU Wien beinhaltet auch ein privat nutzbares, unentgeltliches Familienkonto, welches nach Stornierung der Lizenz - allerdings entgeltlich - weitergenutzt werden kann. Ein bereits vorhandenes Familienkonto kann an eine TU-Wien-Lizenz gekoppelt werden, wodurch für die Dauer der Koppelung keine Kosten anfallen.
Weitere Informationen zur Nutzung von Passwort-Managern und Sicherheitsfragen generell finden Sie im coLab unter IT Security Empfehlungen.
Bestellung
Beide Campussoftware-Produkte, 1password-Teammitglied und 1password-Gruppenadmin, können über TU Shop bestellt werden.
3. Virenschutz
Viren nerven in allen Belangen!
Über das Internet sind Rechner 24 Stunden am Tag, 365 Tage im Jahr digitalen Bedrohungen ausgesetzt. Mittlerweile sind über 500 Millionen unterschiedliche Schadsoftwarevarianten bekannt und sie vermehren sich rasant. Um Ihren Rechner vor unliebsamen Zeitgenossen, wie Cryptolocker, Trojaner, Coinminer oder Keylogger zu schützen, ist ein moderner Virenscanner unerlässlich.
Seit Windows 10 ist der „Windows Defender“ direkt in das Betriebssystem integriert. Dieser wurde auch zu einem empfehlenswerten Security-Programm weiterentwickelt. Unabhängig davon welche Sicherheitslösung sie einsetzen, über die integrierte Anwendung „Windows-Sicherheit“ können Sie den Status überwachen. Im Idealfall ist Ihr Rechner genauso gut geschützt, wie der hier abgebildete:
Abb. 4: Windows Sicherheit auf einem Blick
Virenscanner bieten einen guten Basisschutz, aber natürlich kann damit nicht jede Bedrohung gestoppt werden! Letztendlich entscheiden immer Sie ob Sie einen Anhang öffnen oder eine Datei herunterladen. Ein natürliches Misstrauen ist auch im digitalen Umfeld angebracht. Niemand wird Ihnen, Offline wie Online, ohne Gegenleistung das neuste iPhone schenken!
Auch MacOS verfügt mit „Gatekeeper“ über eine integrierte Sicherheitslösung[3]. Dabei handelt sich zwar um keinen vollwertigen Virenscanner, die meisten für MacOS schadhaften Bedrohungen können aber dennoch damit abgewehrt werden.
4. Systemupdates
Damit Endanwender_innen ein Programm verwenden können, muss zuvor ein_e Softwareentwickler_in dem Rechner die erwartete Funktionalität beibringen. Dabei handelt es sich um einen als „Programmieren“ genannten Prozess. Aktuelle Betriebssysteme, wie beispielsweise Windows 10, bauen dabei im Hintergrund auf 50 – 60 Millionen Zeilen Programmcode auf. Logischerweise ist dieser nicht komplett fehlerfrei – dies ist alleine auf Grund der Menge und der Komplexität nahezu unmöglich.
Bei manchen der darin enthaltenen Fehler handelt es sich um sicherheitsrelevante Probleme. Über diese könnte ein_e Angreifer_in beispielsweise einen fremden Rechner unter seine_ihre Kontrolle bringen. Dementsprechend ist es wichtig, alle vom jeweiligen Softwarehersteller bereitgestellten Updates zeitnah zu installieren. Dadurch werden neu bekanntgewordene Sicherheitsprobleme behoben. Unter Windows 10 kann der aktuelle Updatestatus über die Anwendung „Nach Updates suchen“ überprüft werden. Im besten Fall ist der eigenen Rechner dabei auf dem neusten Stand, wodurch alle bisher bekannten Sicherheitslöcher behoben sind. Falls bei Ihnen Updates fehlen, empfiehlt es sich, diese so schnell wie möglich nachzuinstallieren.
Abb. 5: Windows Systemupdate
Über die Schaltfläche „Erweiterte Optionen“ sollte außerdem sichergestellt werden, dass alle von Microsoft bereitgestellten Updates installiert und entsprechende Benachrichtigungen angezeigt werden.
Abb. 6: Erweiterte Optionen
5. Festplattenverschlüsselung
Stellen Sie sich vor: Sie kommen mit dem Flieger endlich am Zielflughafen an und warten auf Ihr Gepäck. In weniger als einer Stunde haben Sie ein wichtiges Meeting, aber Ihr Firmenlaptop ist nicht mehr aufzufinden. Ein Supergau für Sie, aber auch für das Unternehmen! Denn spätestens seit Einführung der Datenschutzgrundverordnung (DSGVO) genießen sämtliche personenbezogenen Daten einen zusätzlichen Schutz.
Darum sollten alle Endgeräte mit einer Festplattenverschlüsselung vor unberechtigten Datenzugriffen geschützt werden. Ist ein PC, Laptop oder Smartphone einmal verschlüsselt, kann nur mit Kenntnis der richtigen Passwörter wieder auf die darauf gespeicherten Informationen zugegriffen werden.
Neuere Smartphones (iOS und Android) sind von vornherein verschlüsselt. Auch neuere Rechner der Marke Apple sind mit einer Technologie namens FileVault standardmäßig bereits verschlüsselt.
Bei neueren Intel mit T2 chip* sowie den Apple SoC M1/M2 Mac's gibt es aber immer eine Hardware-Verschlüsselung**. Daher ist bei älteren Intel Systemen ohne diesen T2 Chip, FileVault erst zu aktivieren.
(* ) Ist ein T2 chip vorhanden? Überprüfen Sie im Apple Menu → Über diesen Mac → Systembericht → Controller: wenn hier ein Apple T2-Sicherheits-Chip angeführt wird, ist die Festplatte bereits per Hardware verschlüsselt
(** ) FileVault kann aber jederzeit noch dazu eingeschaltet werden (die Festplatte wäre dann also doppelt verschlüsselt - das geht aber zu Lasten der Performance)
(!) bitte denken sie auch an die Verschlüsselung ihres(r) Backups
Schützen des Time Machine-Backup-Volumes auf dem Mac: https://support.apple.com/de-at/guide/mac-help/mh21241/12.0/mac/12.0
Um bei Windows 10 Rechnern (ausgenommen ist die Version Windows 10 Home) die eingebaute Festplatte vor unberechtigten Zugriffen zu schützen, kann die sogenannte „Bitlocker Technologie“ verwendet werden, die bei Windows 10 integriert ist.
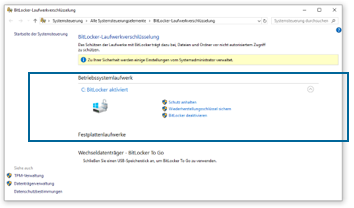
Dazu geben Sie im Suchfeld links unten den Begriff „BitLocker“ ein. Damit gelangen sie zur „BitLocker-Verwaltung“. Dort klicken Sie auf „BitLocker aktivieren“. Damit ist ihre Festplatte verschlüsselt und jegliche Information wird nun entsprechend abgesichert auf dem Gerät gespeichert. Diebe können nicht mehr auf die Dateien zugreifen – vorausgesetzt, Sie verwenden ein sicheres Passwort für Ihren Rechner.
Der folgende Screenshot zeigt die optimale Konfiguration: BitLocker ist für das Betriebssystemlaufwerk aktiv:
Abb. 7: Windows Suche
Abb. 8: BitLocker-Laufwerkverschlüsselung
6. Bildschirmsperre
Sie bearbeiten einen Förderantrag für ein EU-Projekt und berechnen die voraussichtlichen Lohnkosten der Projektmitarbeiter_innen, als ihr Handy läutet. Um die Kolleg_innen im Büro nicht zu stören, stehen Sie „nur kurz auf“ und begeben sich ins Besprechungszimmer, um zu telefonieren. Da die Kollegin am Telefon doch mehr über die letzte Konferenz zu berichten hat als erwartet, dauert das Telefonat eine halbe Stunde. Anschließend kehren Sie wieder auf Ihren Platz zurück.
Um zu verhindern, dass unbefugte Personen die von Ihnen bearbeiteten Daten einsehen oder auf Ihre Daten zugreifen können, muss bei jedem (!) Verlassen des Arbeitsplatzes (auch im Homeoffice) der Bildschirm gesperrt werden. Auch dann, wenn Sie alleine im Büro sind und Sie die Türe versperren, da es Personen gibt, wie beispielsweise das Reinigungspersonal, die theoretisch jederzeit Ihr Büro betreten könnten.
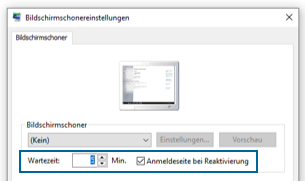
Wenn Sie im Suchfeld am linken unteren Bildschirmrand nach „Bildschirmschoner“ suchen, erhalten Sie die Option „Bildschirmschoner ändern“. Bei Klicken auf diese Option erscheint das Fenster „Bildschirmschonereinstellungen“. Hier kann per Anklicken des Häkchens „Anmeldeseite bei Reaktivierung“ die „Wartezeit“ bei Inaktivität konfiguriert werden, also die Zeit nachdem der Rechner gesperrt wird, wenn nicht gearbeitet wird (Empfehlung 5. – 10 Minuten). Zum Entsperren des Rechners ist dann die Eingabe des Passworts notwendig.
Abb. 9: Windows Suche
Abb. 10: Bildschirmschonereinstellung
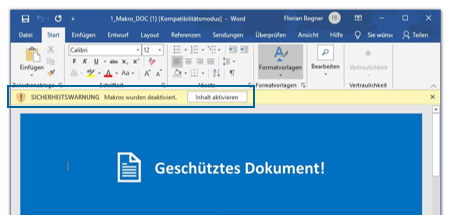
7. Office Makros
Microsoft Office bietet seit jeher sehr weitreichende Automatisierungsfunktionen. Diese als „Office Makro“ bekannte Funktionalität wird mittlerweile jedoch sehr häufig für die initiale Infektion mit Schadsoftware missbraucht. Benutzer_innen werden dabei verleitet, der Makroausführung durch einen Klick auf „Inhalt aktivieren“ zuzustimmen.
Abb. 11: Makros "Inhalt aktivieren"
Kann der_die Anwender_in tatsächlich zu diesem „falschen Klick“ verleitet werden, wird im Hintergrund eine Schadsoftware nachgeladen und der_die Angreifer_in erhält die Kontrolle über den betroffenen PC oder im schlimmsten Fall über das ganze Netzwerk in dem sich der_die Anwenderin befindet. Daher ist es entscheidend, nur bei wirklich vertrauenswürdigen Dokumenten der Makroausführung zuzustimmen.
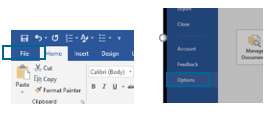
Sollten Sie die weitreichenden Automatisierungsfunktionen generell nicht benötigen, wird empfohlen, diese von vornherein zu deaktivieren und nur dann zu aktivieren, wenn sie tatsächlich benötigt werden. Dazu muss in Microsoft Word und Excel über das Trust Center (im Reiter „Datei (File)“ auf „Optionen (Options)“ è Trust Center è Einstellungen für das Trust Center) im Bereich Makroeinstellungen die folgende Option aktiviert werden:
Abb. 12: Makros deaktivieren
Achtung: selbst wenn Sie Makros einsetzen, darf nie die Option „Alle Makros aktivieren“ ausgewählt werden. Bereits das Öffnen einer Office Datei kann ansonsten bereits zur Infektion des Rechners ausreichen.
8. Bewusste Wahl eines Standardbrowsers
Steigen wir „ins Internet ein“, nutzen wir dazu einen Webbrowser. Dieser zeigt öffentlich bereitgestellte Inhalte an und erlaubt uns, mit diesen zu interagieren. Dabei ist darauf zu achten, einen sicheren Webbrowser zu verwenden. Andernfalls ist es Hacker_innen relativ einfach möglich, Schadsoftware auf einem Rechner zu installieren, uns zu überwachen und sensible Daten (wie beispielsweise Kreditkarteninformationen) zu stehlen.
Empfohlen werden folgende Browser:
- Microsoft Edge: Ein erst kürzlich von Microsoft veröffentlichter Browser. Dieser ist seit Windows 10 im Betriebssystem integriert.
- Mozilla Firefox: Ein besonders anpassbarer Webbrowser mit vielen Optionen. Der Download ist kostenlos unter der folgenden URL möglich: https://www.mozilla.org/de/firefox/
- Google Chrome: Ein von Google bereitgestellter Browser mit dem Fokus auf Geschwindigkeit: https://www.google.com/chrome/
Alle modernen Browser bieten die Möglichkeit, Werbung im Internet automatisch zu blockieren. Dazu kann beispielsweise die Erweiterung „uBlock“ verwendet werden. Diese Erweiterung kann über den Aufruf des untenstehenden Links bei den oben angeführten Browsern aktiviert werden.
- uBlock für Microsoft Edge: https://microsoftedge.microsoft.com/addons/detail/ublock-origin/odfafepnkmbhccpbejgmiehpchacaeak
- uBlock für Mozilla Firefox: https://addons.mozilla.org/de/firefox/addon/ublock-origin/
- uBlock für Google Chrome: https://chrome.google.com/webstore/detail/ublock-origin/cjpalhdlnbpafiamejdnhcphjbkeiagm?hl=de
9. Dateierweiterungen anzeigen & erkennen
Tagtäglich arbeiten wir mit einer Vielzahl unterschiedlicher Dokumente. Wenn eine Datei mittels Doppelklick geöffnet wird, entscheiden moderne Betriebssysteme anhand der Dateiendung (alles nach dem letzten Punkt) welches Programm für die Anzeige geeignet ist.
Leider gibt es auch einige als gefährlich einzustufende Dokumententypen, wie beispielsweise .vbs (Visual Basic Script), .js (Javascript) und .hta (HTML Application). Ein Doppelklick darauf kann zur Infektion des eigenen Rechners führen. Damit diese richtig erkannt und anschließend direkt gelöscht werden können, ist es wichtig die Dateinamenerweiterungen einblenden zu lassen. Wie im folgenden Screenshot dargestellt, muss dazu die Checkbox „Dateinamenerweiterungen“ im „Ansicht“-Reiter des Windows Explorer aktiviert werden.
Abb. 13: Dateinamenerweiterung aktivieren
Da es eine Vielzahl potentiell gefährlicher Dateitypen gibt, ist es nicht möglich alle aufzulisten. Einfacher und auch sicherer ist es, die als unbedenklich einzustufenden Datentypen zu nennen. Die folgende Tabelle listet die am häufigsten anzutreffenden Dateierweiterungen auf, welche bedenkenlos geöffnet werden können:
Dateierweiterung | Beschreibung |
.doc | Word Datei (Achtung bei Makros) |
.docx | Neue Word Datei |
.xls | Excel Datei (Achtung bei Makros) |
.xlsx | Neue Excel Datei |
.ppt | PowerPoint Datei |
.pptx | Neue Powerpoint Datei |
Portable Document Format (PDF) Datei | |
.jpg, .jpeg, .png, .gif | Verbreitete Bilddateien |
.zip | Archiv Datei |
.txt | Klartextdatei |
Sollten Sie eine unbekannte Datei erhalten, empfiehlt es sich (bevor Sie diese Öffnen) bei Ihrer IT nachzufragen.
10. Separate Admin-Benutzer_innen
Historisch bedingt arbeiten an der TU Wien viele Anwender_innen mit administrativen Berechtigungen. Der Grund dafür liegt darin, dass nur so beispielsweise Updates ausgeführt, neue Programme installiert oder systemrelevante Konfigurationen geändert werden können. Problematisch wird dieser Ansatz jedoch sobald eine Schadsoftware auf dem Rechner ausgeführt wird. Diese kann nun nämlich auf alle Daten zugreifen und so auch Dateien anderer Benutzer_innen löschen oder sich im Netzwerk ausbreiten. Im schlimmsten Fall könnten also ganze Rechnergruppen ausfallen.
Deshalb wird empfohlen, nie mit administrativen Berechtigungen zu arbeiten, sondern stattdessen eine_n separate_n Admin-Benutzer_in einzusetzen.
Dazu muss im ersten Schritt überprüft werden, ob der_die bisherige „Benutzer_in“ über administrative Berechtigungen verfügt. Über eine Windows Suche nach dem Schlüsselwort „Ihre Kontoinformationen“ kann dies einfach festgestellt werden. Der im Folgenden dargestellte Benutzer verfügt über administrative Berechtigungen und sollte daher abgesichert werden:
Abb. 14: Kontoinformationen abrufen
Da der genaue Prozess mehrere Arbeitsschritte umfasst, verweisen wir hier auf das von Microsoft bereitgestellte Video „Erstellen eines lokalen Benutzer- oder Administratorkontos in Windows 10“. Dieses erklärt die notwendige Konfigurationsänderungen im Detail: https://support.microsoft.com/de-at/help/4026923/windows-10-create-a-local-user-or-administrator-account
Bei Fragen können Sie sich auch an Ihre_n IT Betreuer_in wenden. Diese_r kann bei der Konfiguration unterstützen und allfällige Fragen kompetent beantworten.
[1] Eine Konfigurationsanleitung finden Sie unter: https://support.apple.com/de-at/HT201250 (zuletzt abgerufen am 25.09.2020).
[2] Weitere Anleitungen zur Nutzung des „Dateiversionsverlauf“, sowie zur Wiederherstellung von Dateien finden Sie unter: https://support.microsoft.com/de-de/help/17128/windows-8-file-history (zuletzt abgerufen am 23.09.2020).
[3] Siehe: https://support.apple.com/de-at/HT202491 (zuletzt abgerufen am 23.09.2020).










6 Kommentare
Marianne Rudigier sagt:
Gregor Hartweger ergänzen um:
Wobei Punkt 2 und 3 eigentlich zu den Homeoffice-Tipps gehören. Wie siehst du das?
Gregor Hartweger sagt:
Zu 1) Die Firewall ist im Windows Defender intergriert und sollte standardmäßig aktiviert sein. Heutzutage fällt das alles unter Endpointsecurity! Der Sophos, der als Campussoftware angeboten wird, ist nur für PCs verwendbar, dort zwar gut, aber ich evaluiere ein paar Varianten, die universell einsetzbar sind (alle Plattformen und Mobile Geräte).
2,3 ) Ja, das wäre Home-Office, passt aber zur Datensicherheit. Vielleicht sollten wir das querverlinken oder hat das VR anders gemeint?
Die IT Security Empfehlungen zielen genau auf die verwendete Hardware, die entweder Infrastruktur darstellt oder auf sie zugreift. Die Geräte (die Du im Mail beschreibst) sind damit eigentlich auch gemeint, allerdings anders beschrieben. Die WLAN Router sind eine notwendige dazwischenliegende Hardware, die eventuell auch zu den Geräten kommen könnte.
Martin Rathmayer sagt:
bezüglich Festplattenverschlüsselung: Natürlich ist die „Bitlocker Technologie“ auch bei Windows 10 Home verfügbar, allerdings muss sie dort über die Commandline und kann nicht über das GUI aktiviert werden. Nach der Aktivierung ist sie dann auch im GUI sichtbar.
Gregor Hartweger sagt:
Ja, das stimmt schon, aber wir wollten ganz Bewusst keine Commandline aufrufen müssen, weil das für den/die reine Anwender_in auch eine Fehlerquelle darstellen könnte. Wir könnten das eventuell bei den Empfehlungen für Administrator_innen ergänzen?
Martin Rathmayer sagt:
Da hast Du allerdings Recht. Da muss man wissen, was man tut. Das kann ins Auge gehen.
Gregor Hartweger sagt:
Du meinst "manage‐bde ‐on C:" oder?
Ich hätte das unter den Punkt 5. Festplattenverschlüsselung bei den "IT Security Empfehlungen für Administrator_innen" eingefügt.
Magst Du das dort hinzufügen?